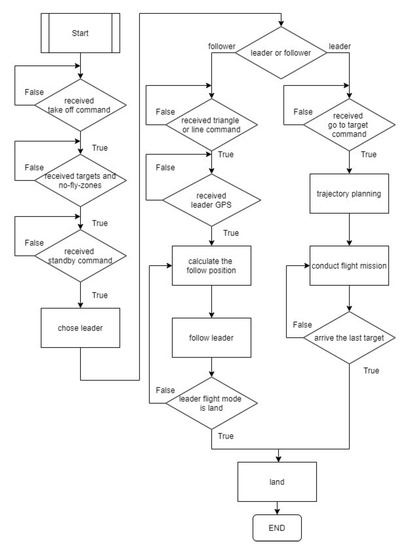
Applied Sciences | Free Full-Text | UAV Swarm Real-Time Rerouting by Edge Computing D* Lite Algorithm
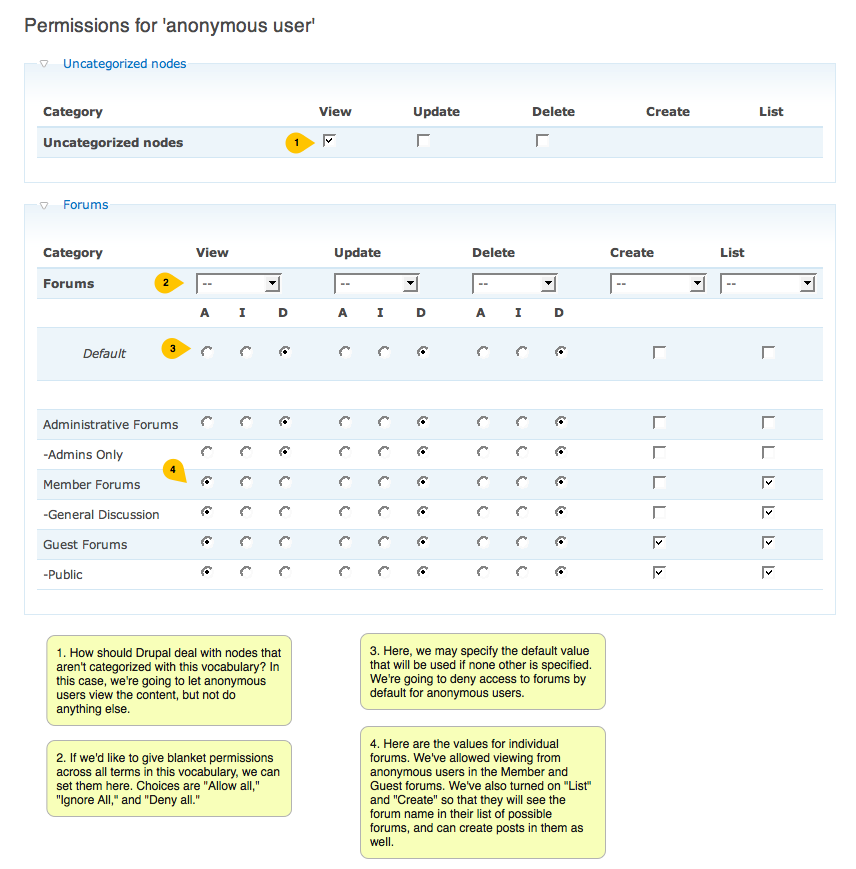
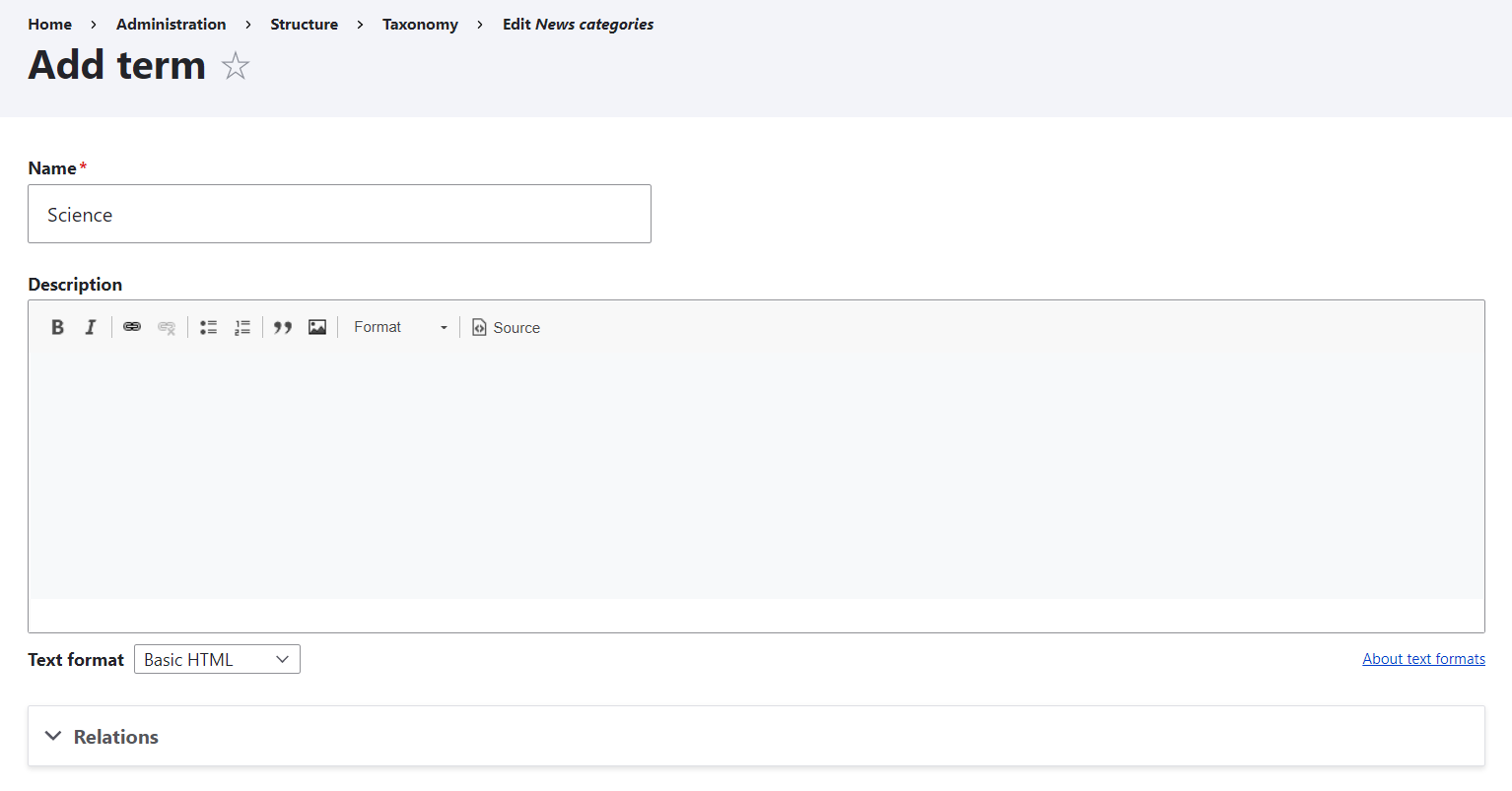
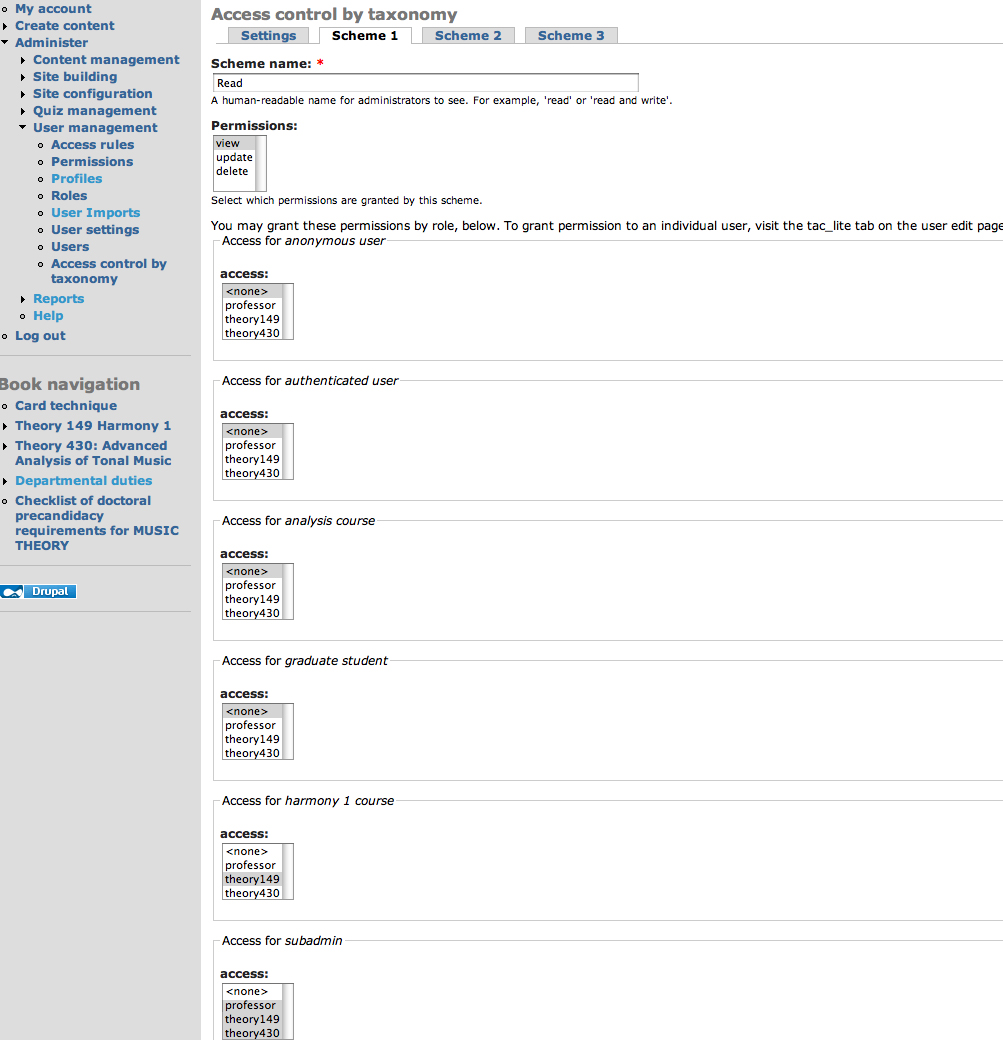
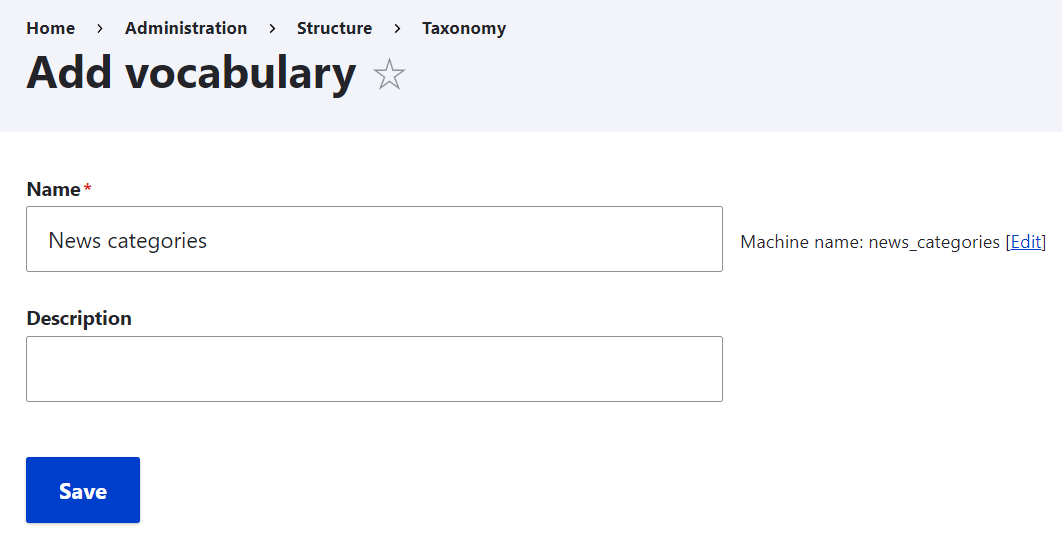
Private forums in Drupal: Forum Access vs. Taxonomy Access vs. Taxonomy Access Control Lite | Lullabot
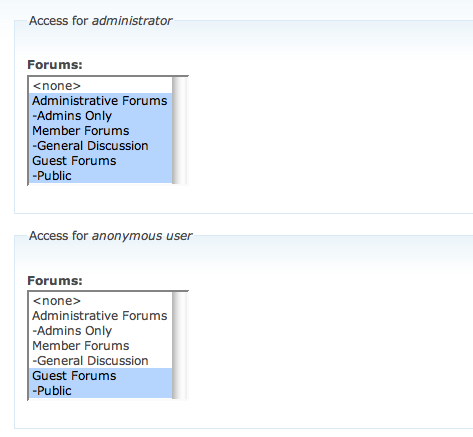
Private forums in Drupal: Forum Access vs. Taxonomy Access vs. Taxonomy Access Control Lite | Lullabot

GSMA | 5G Cybersecurity Knowledge Base - Security | Cyber security, Mobile network operator, Communication networks

Electronics | Free Full-Text | A Coloured Petri Net- and D* Lite-Based Traffic Controller for Automated Guided Vehicles
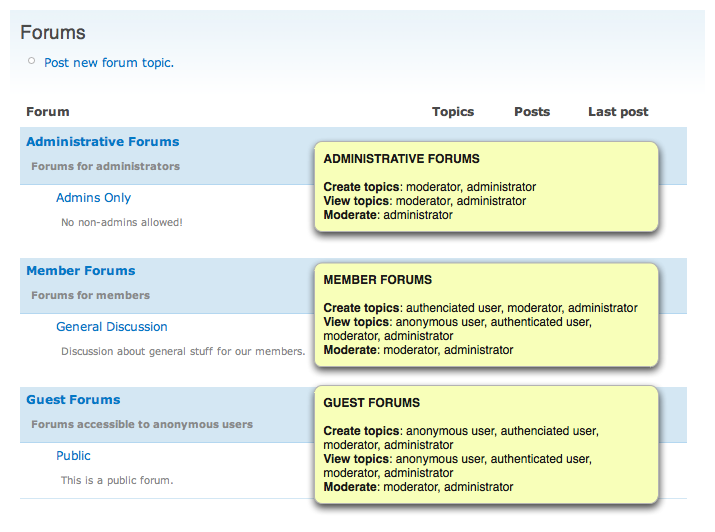
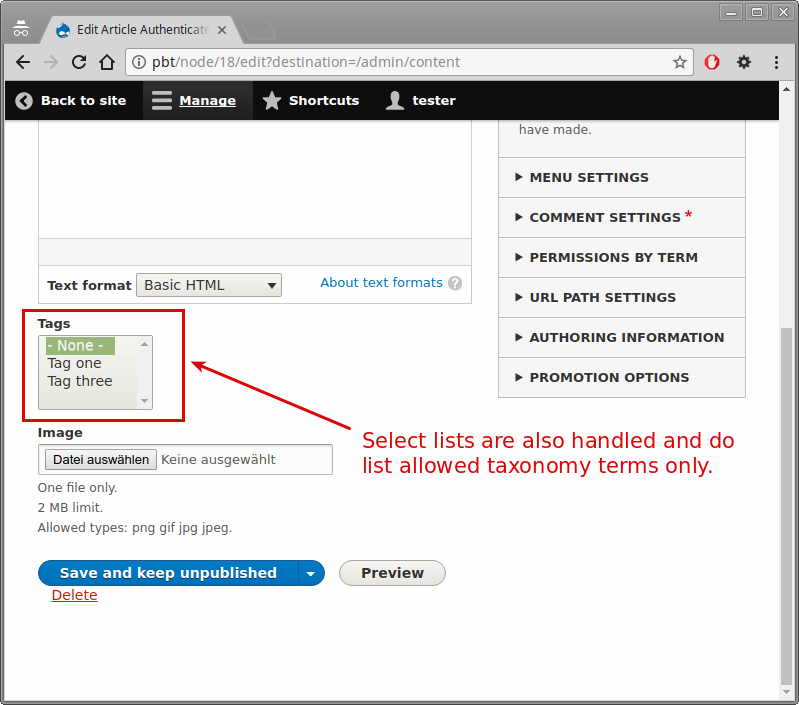
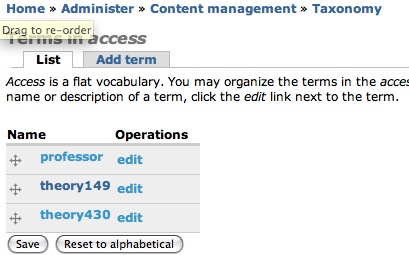
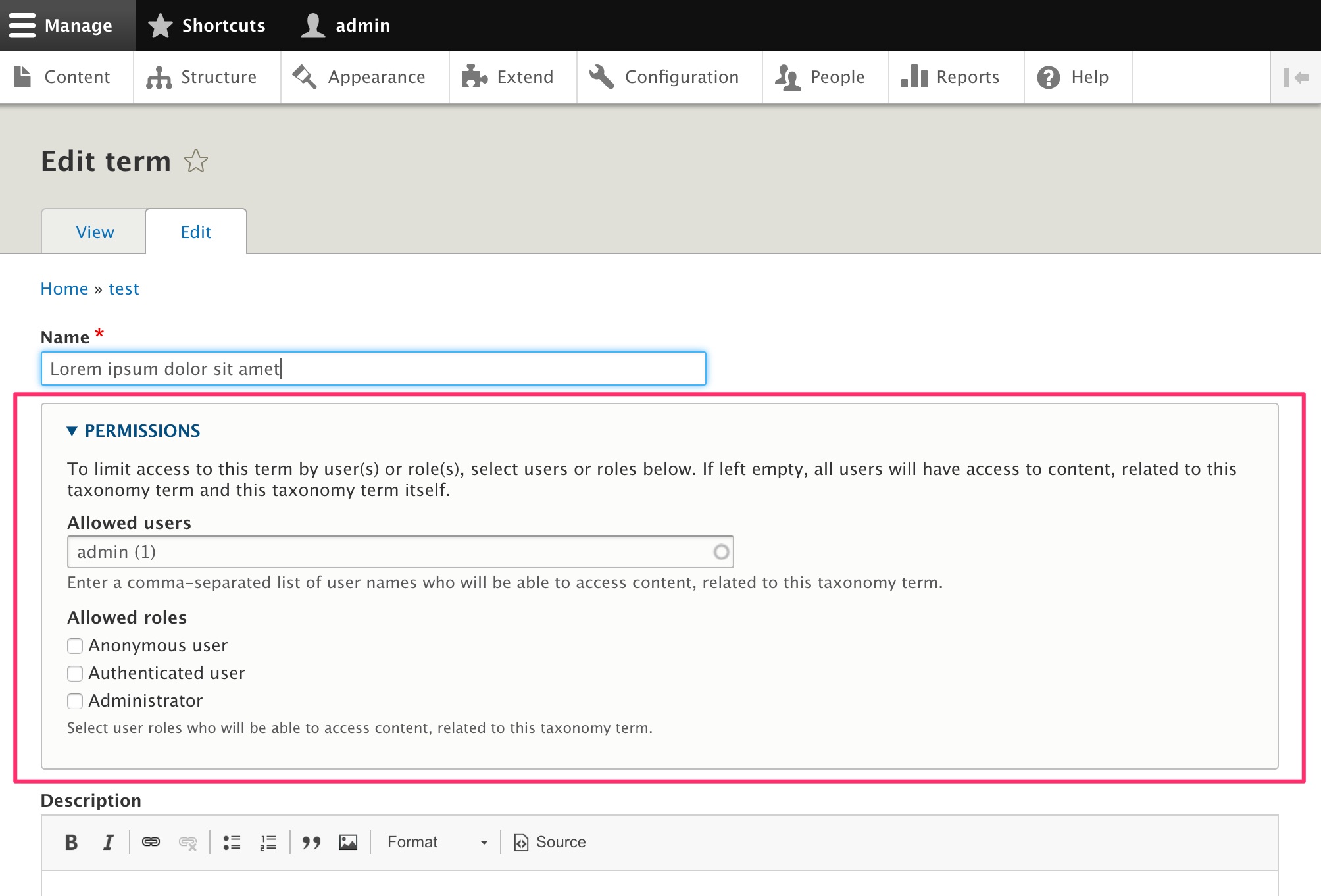
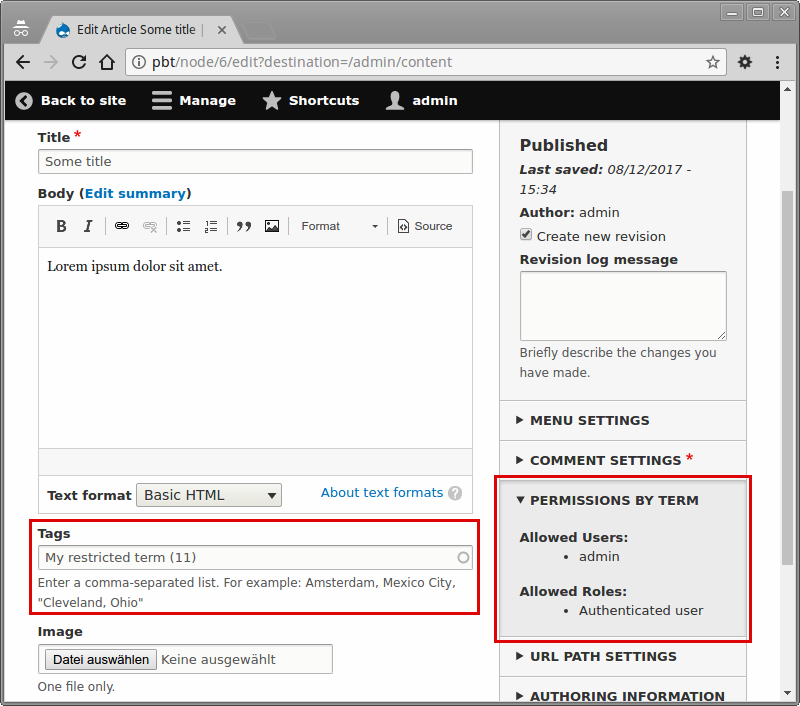
Private forums in Drupal: Forum Access vs. Taxonomy Access vs. Taxonomy Access Control Lite | Lullabot

AI Ops and the Self-Optimization of Resources | Software development life cycle, Optimization, Infrastructure